GitHub - 0x802/MikrotikSploit: MikrotikSploit is a script that searches for and exploits Mikrotik network vulnerabilities

Amazon.com: MikroTik hAP AC RouterBoard, Triple Chain Access Point 802.11ac (RB962UiGS-5HacT2HnT-US) : Electronics
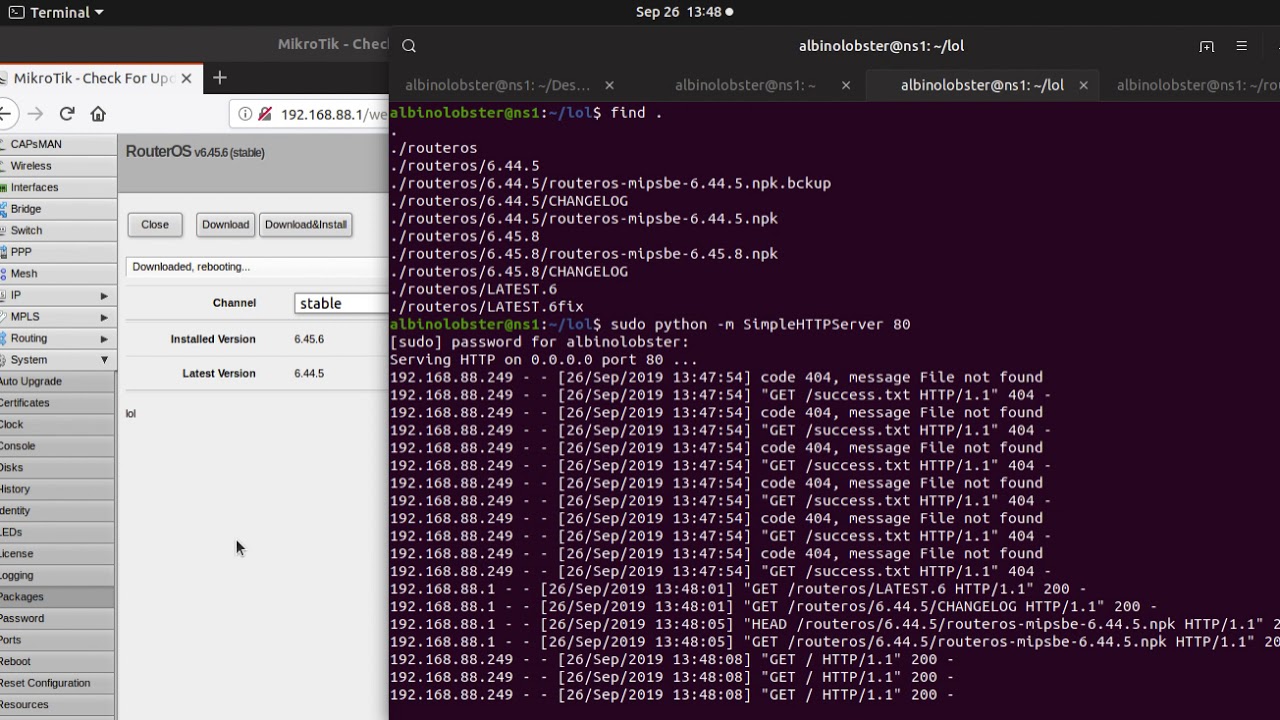
RouterOS: Chain to Root. DNS Request to a Root Busybox Shell | by Jacob Baines | Tenable TechBlog | Medium
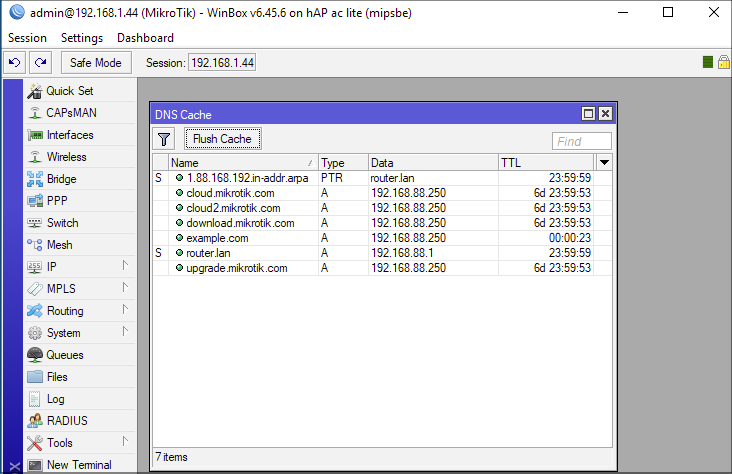
RouterOS: Chain to Root. DNS Request to a Root Busybox Shell | by Jacob Baines | Tenable TechBlog | Medium
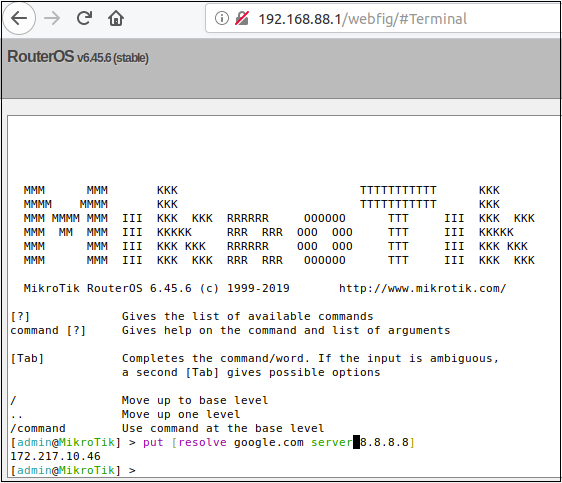
RouterOS: Chain to Root. DNS Request to a Root Busybox Shell | by Jacob Baines | Tenable TechBlog | Medium

hackerfantastic.crypto on Twitter: "Here is "@mikrotik_com RouterOS <= 6.43.7 post-authentication local root arbitrary file creation #0day." On versions prior to 6.40 this can be used to trivially jailbreak a RouterOS device -

![OpenWrt Wiki] MikroTik RouterBoard RB750GL OpenWrt Wiki] MikroTik RouterBoard RB750GL](https://openwrt.org/_media/media/mikrotik/rb750gl_top.jpg)










![OpenWrt Wiki] MikroTik RB750Gr3 OpenWrt Wiki] MikroTik RB750Gr3](https://openwrt.org/_media/media/mikrotik/mikrotik_rb750gr3.png)