Firewall installation and configuration in Kali Linux | Learn Linux CCNA CEH IPv6 Cyber-Security Online
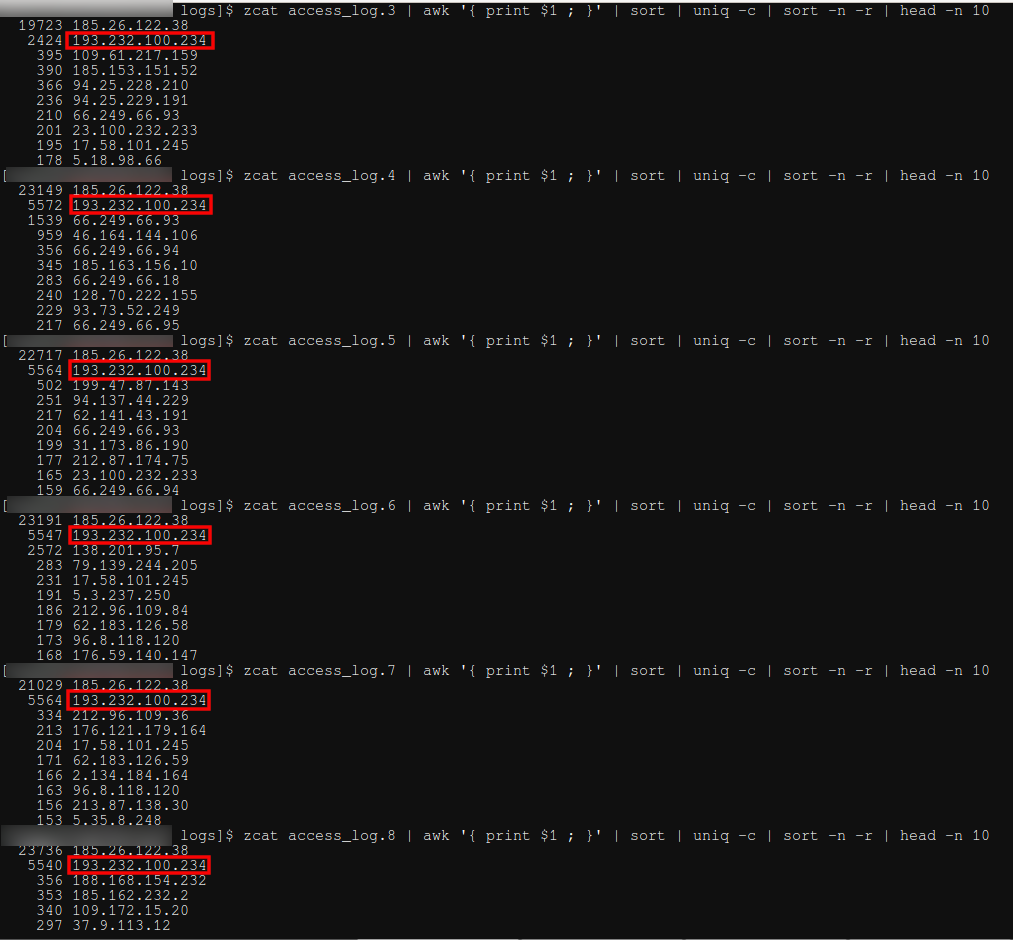
How to search and brute force services on non-standard ports - Ethical hacking and penetration testing

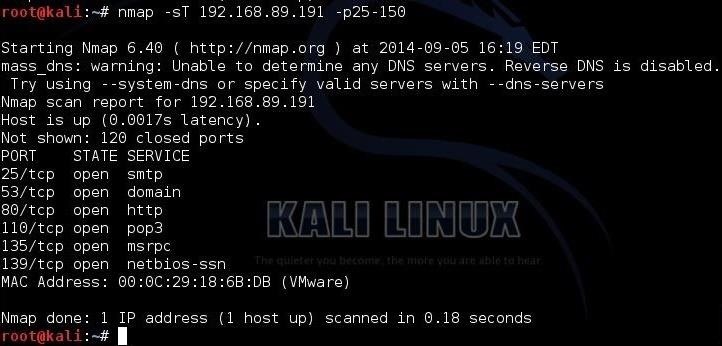
Day 46: How Do Hackers Use Open Ports To Perform Attacks? | Day 46: How Do Hackers Use Open Ports To Perform Attacks? Today I will discuss: 1. Why do hackers search
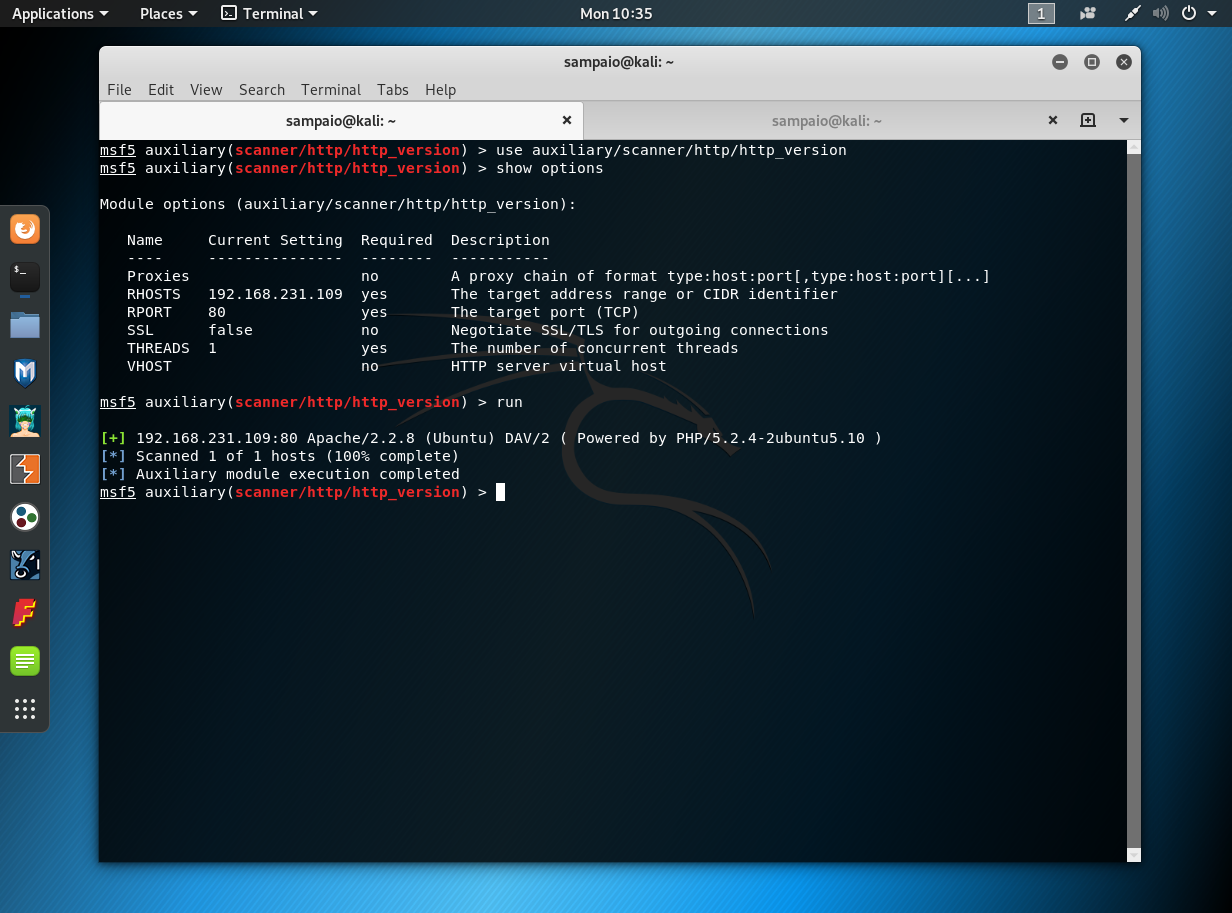
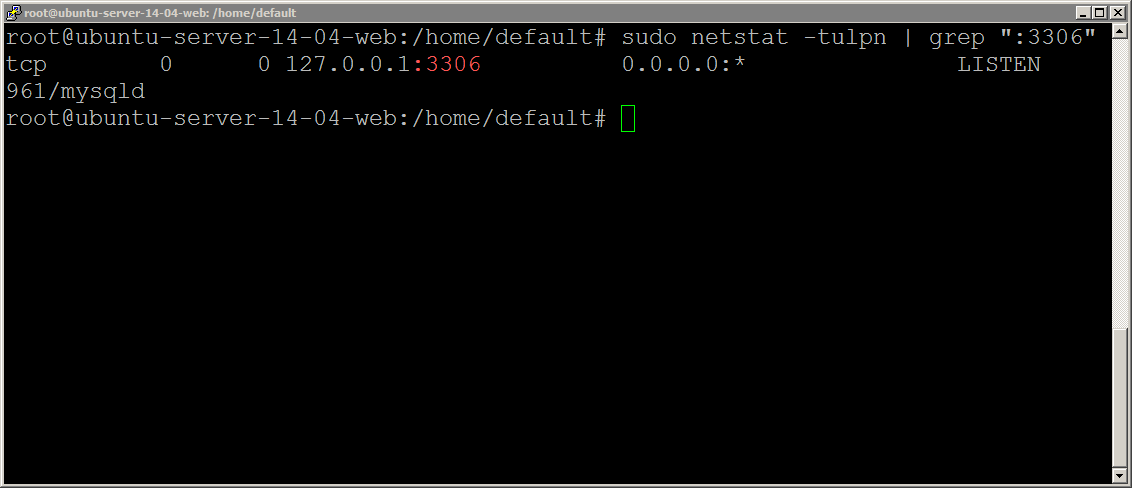
Metasploitable 2: Port 80. Welcome back to part IV in the… | by Miguel Sampaio da Veiga | Hacker Toolbelt | Medium
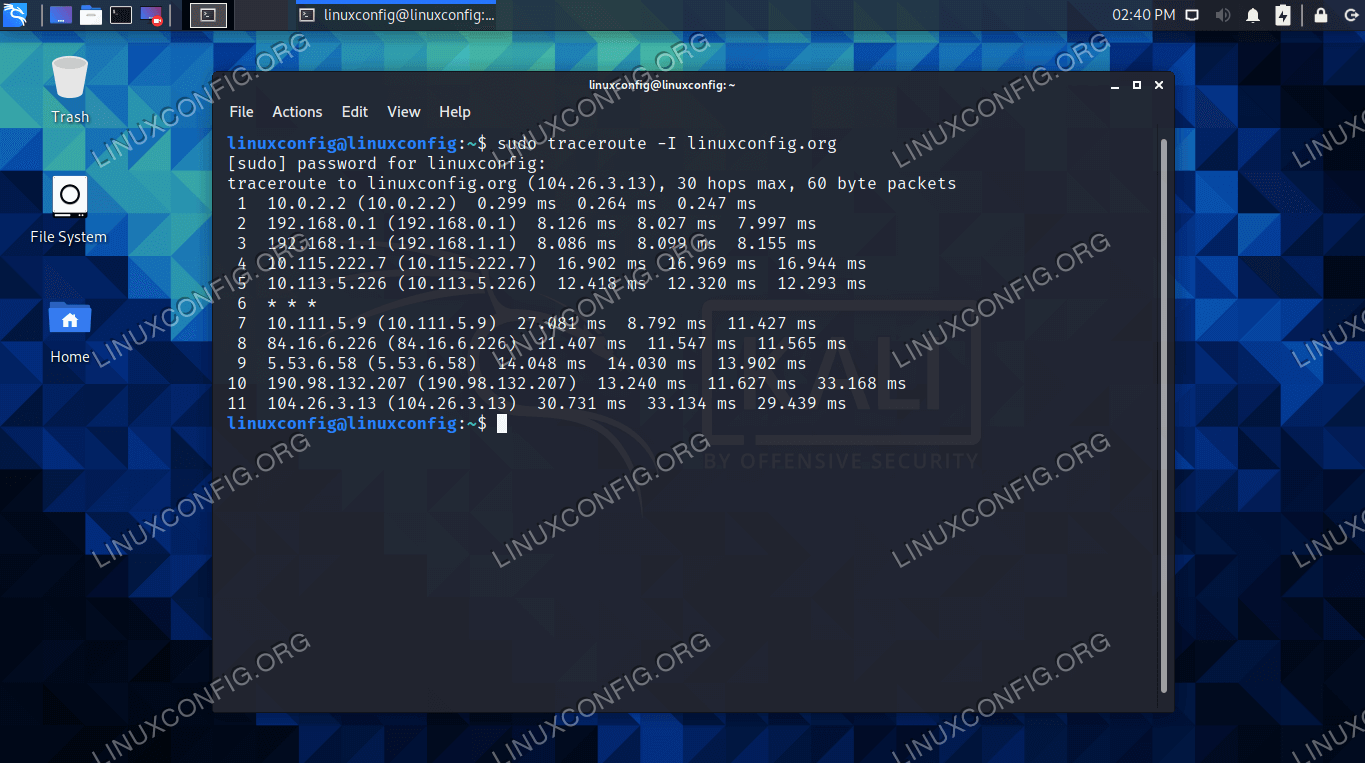

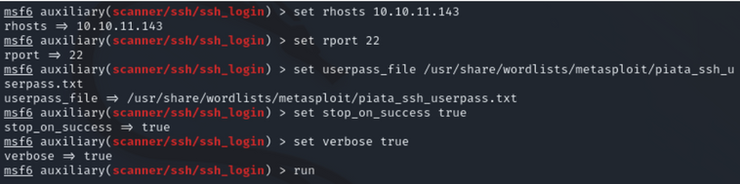






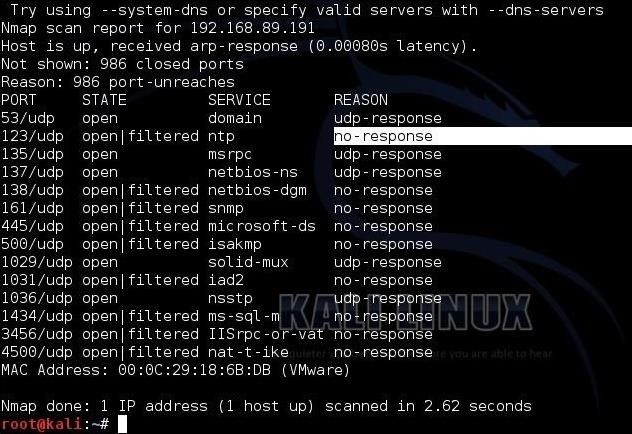



![Hack Windows 10 Remotely over WAN with Metasploit [No Port Forwarding] - Yeah Hub Hack Windows 10 Remotely over WAN with Metasploit [No Port Forwarding] - Yeah Hub](https://www.yeahhub.com/wp-content/uploads/2017/07/windows-10-hacking-ngrok-1.png)