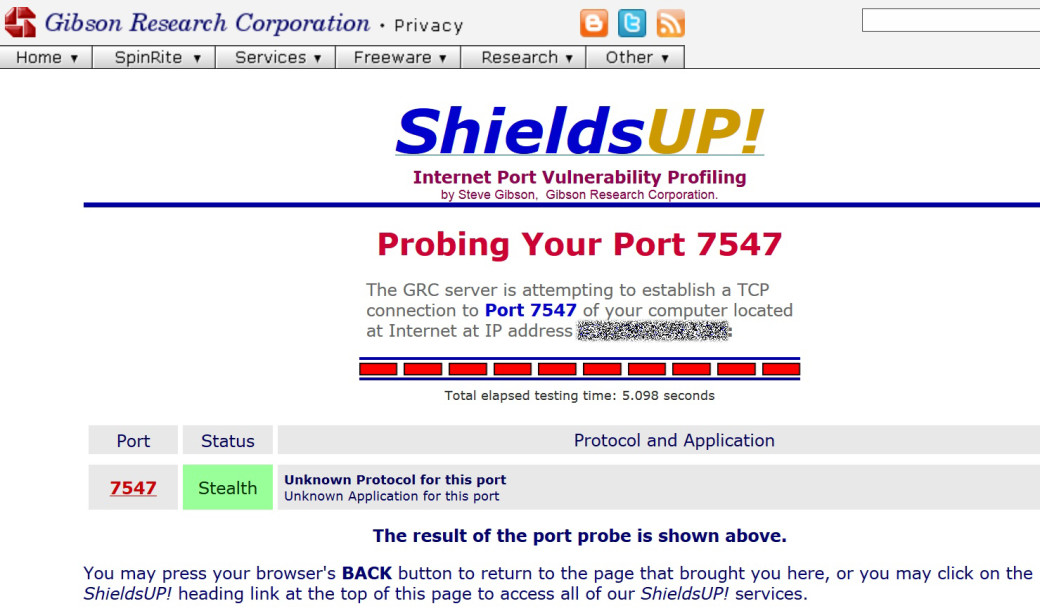
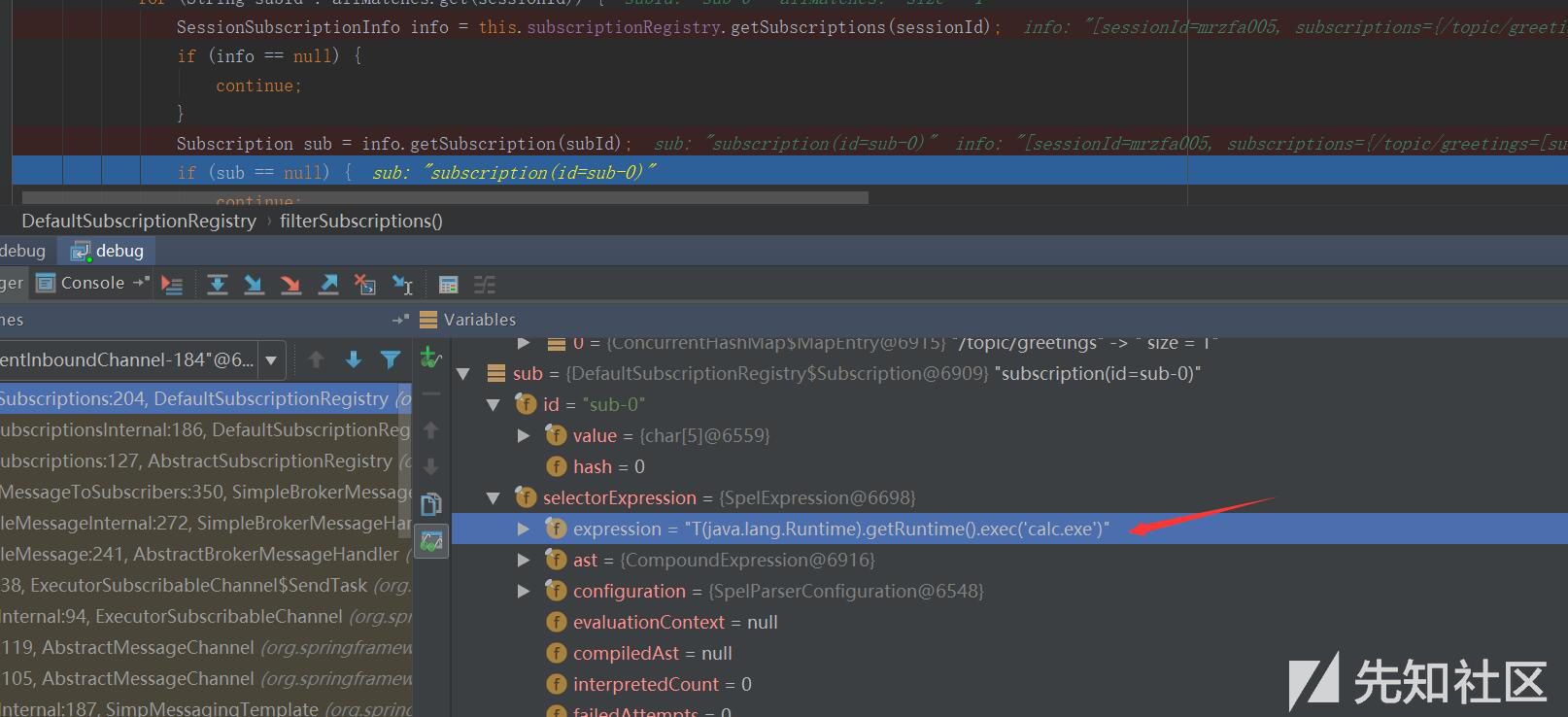
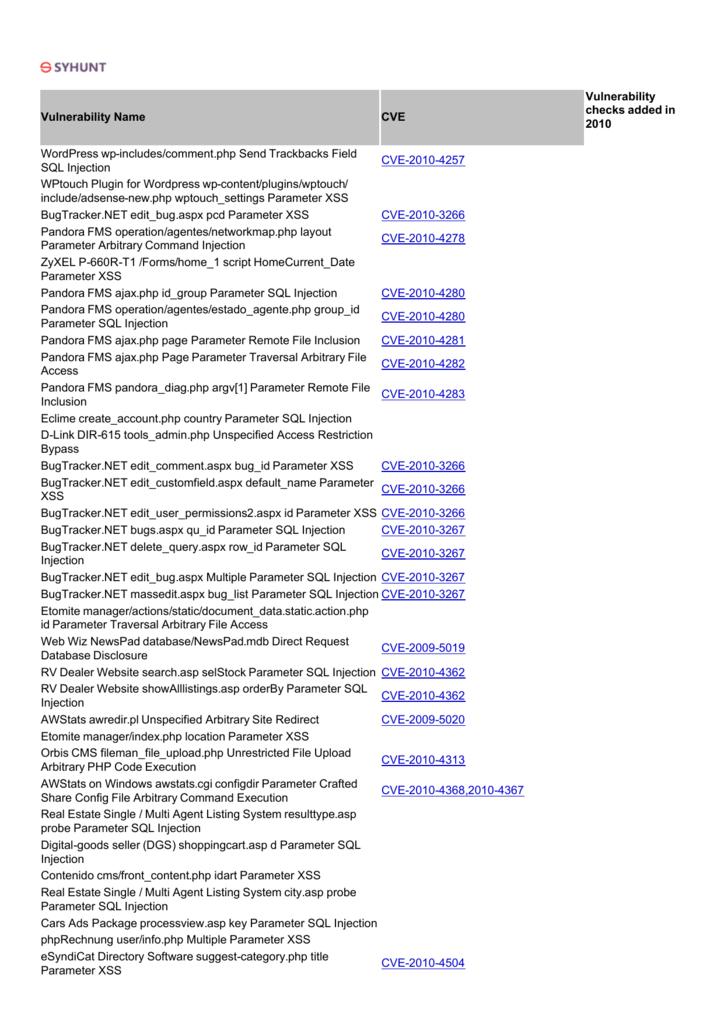
La botnet del router TP-Link è stata utilizzata per anni per inviare SMS a basso costo - (in)sicurezza digitale
CWE-Knowledge-Graph-Based-Twitter-Data-Analysis-for-Cybersecurity/2015tweets.csv at master · nansunsun/CWE-Knowledge-Graph-Based-Twitter-Data-Analysis-for-Cybersecurity · GitHub
Wireless-Router-Vulnerability/TplinkDiagnosticAuthenticatedRCE.txt at master · coincoin7/Wireless-Router-Vulnerability · GitHub