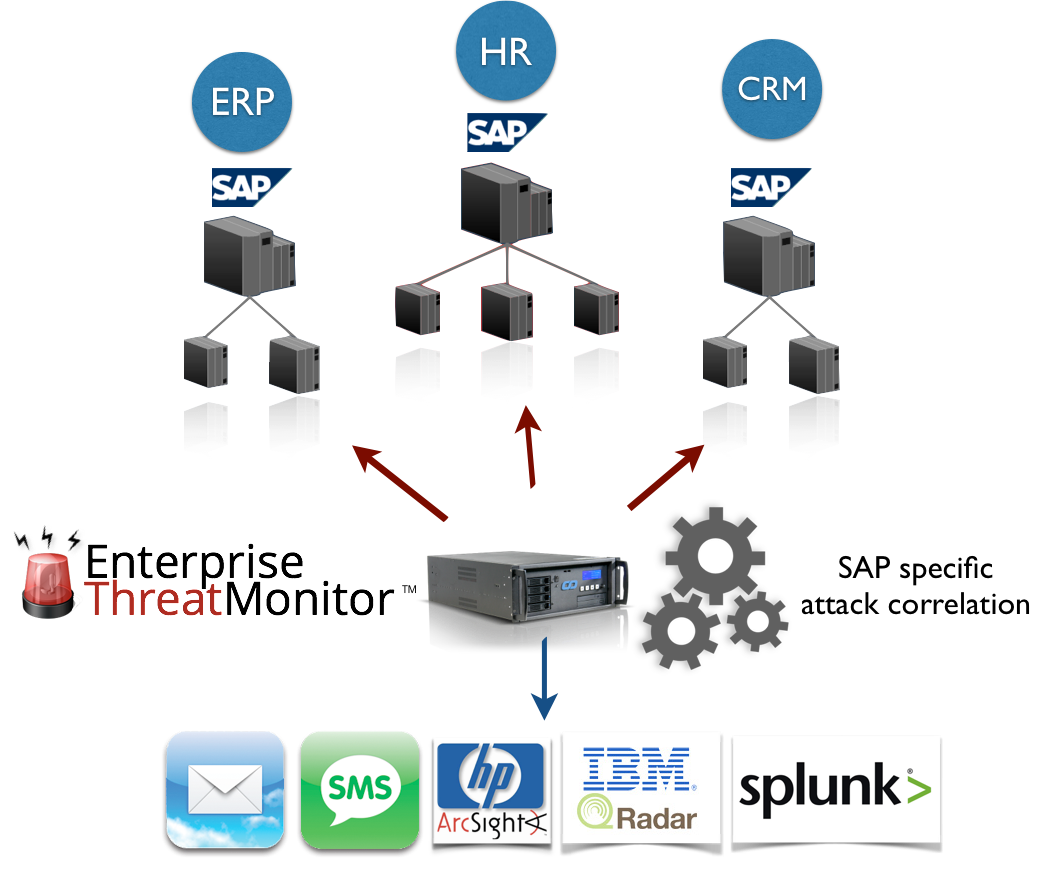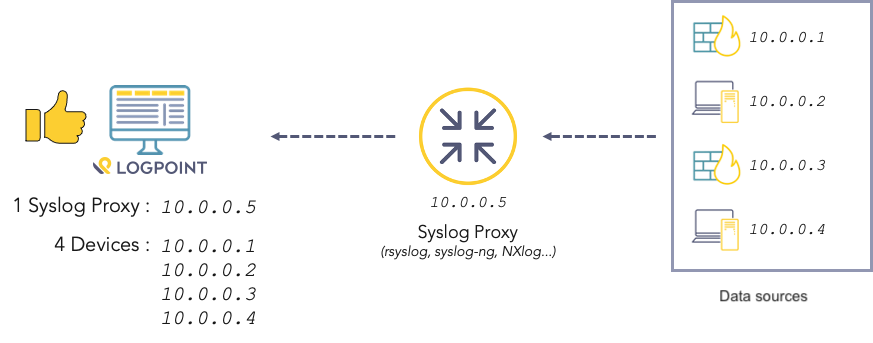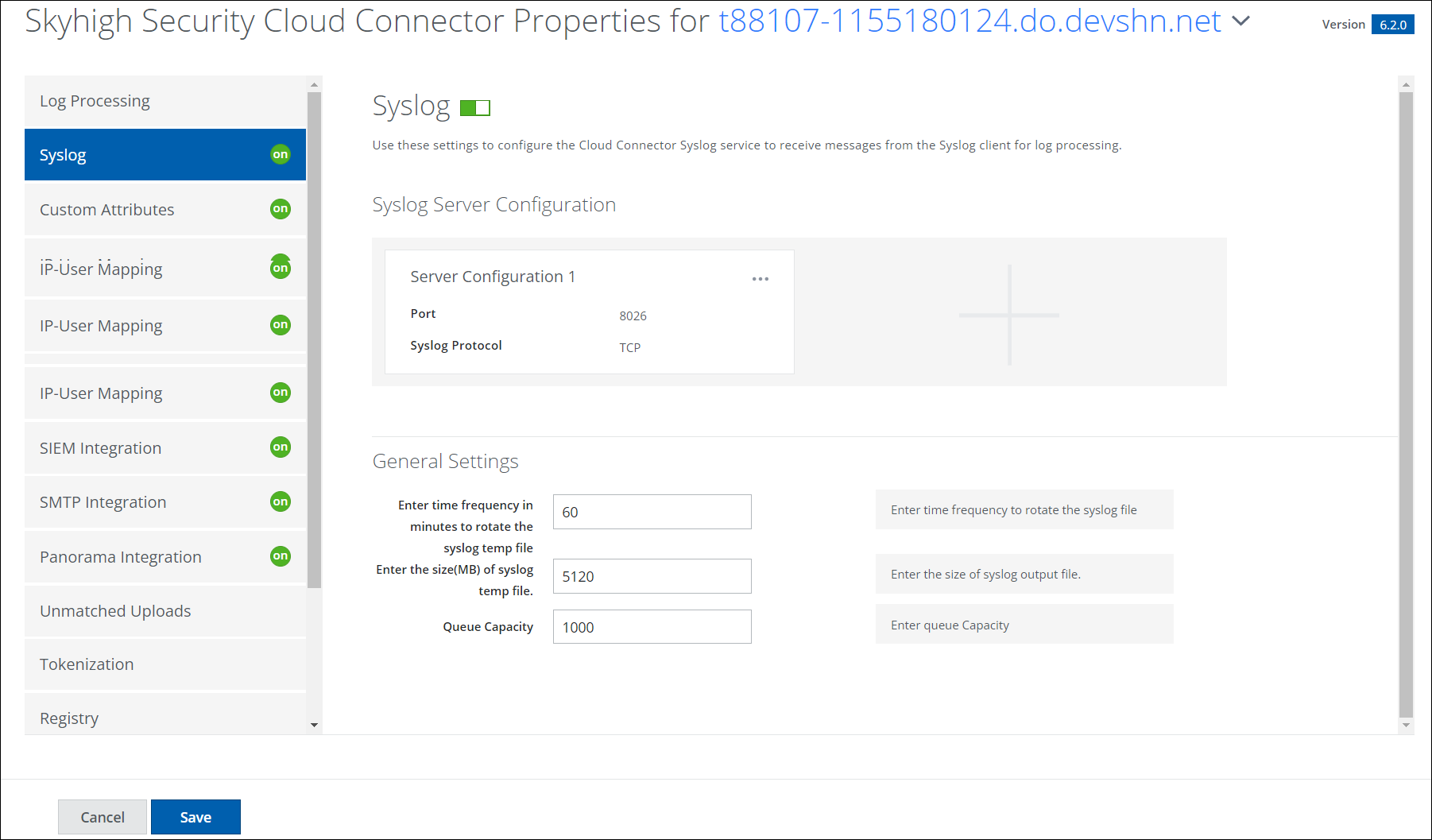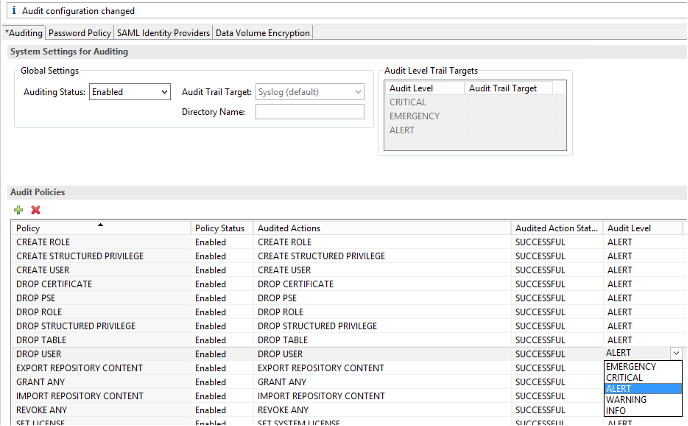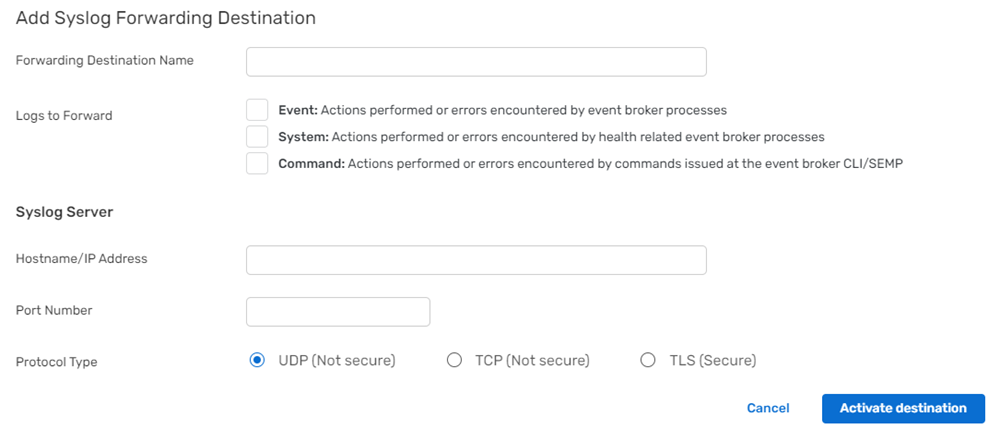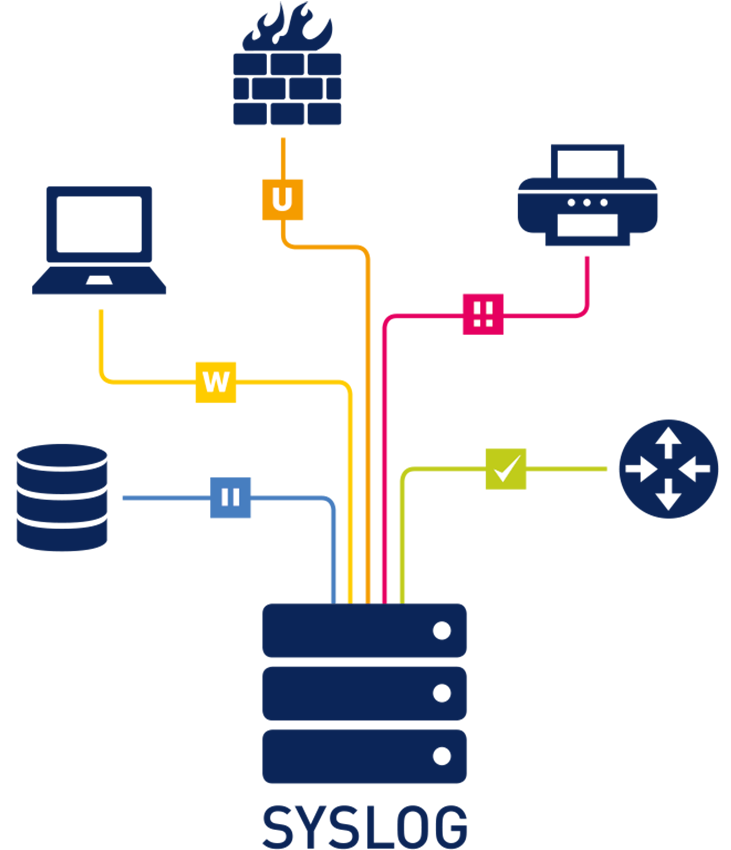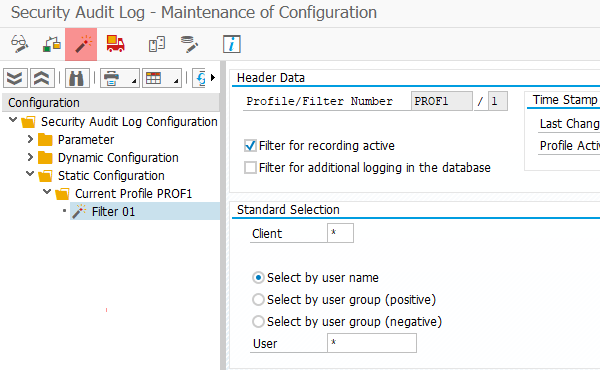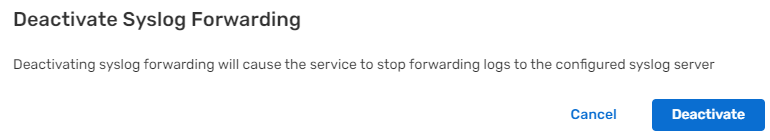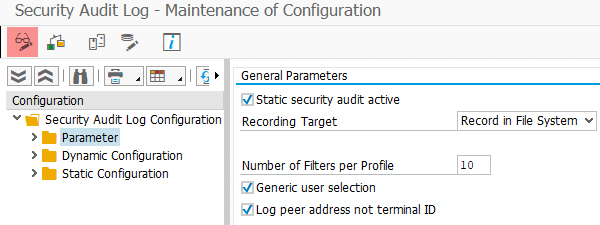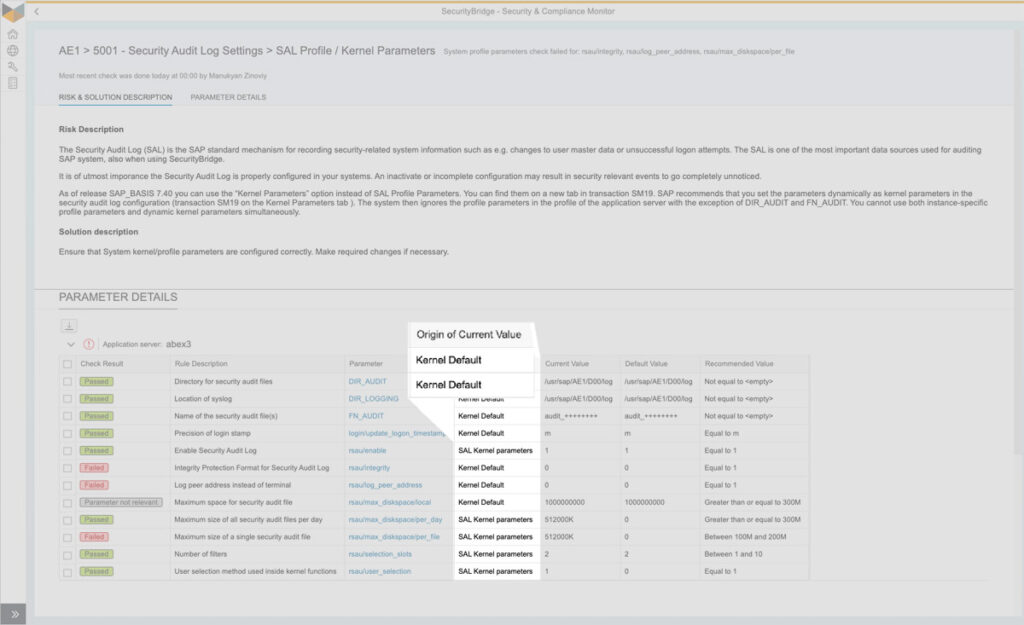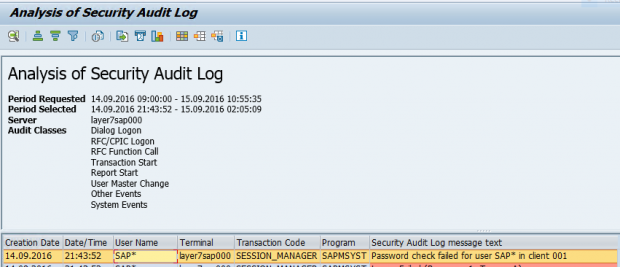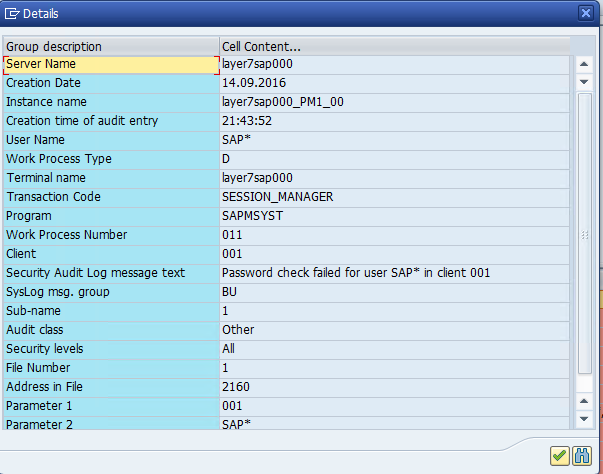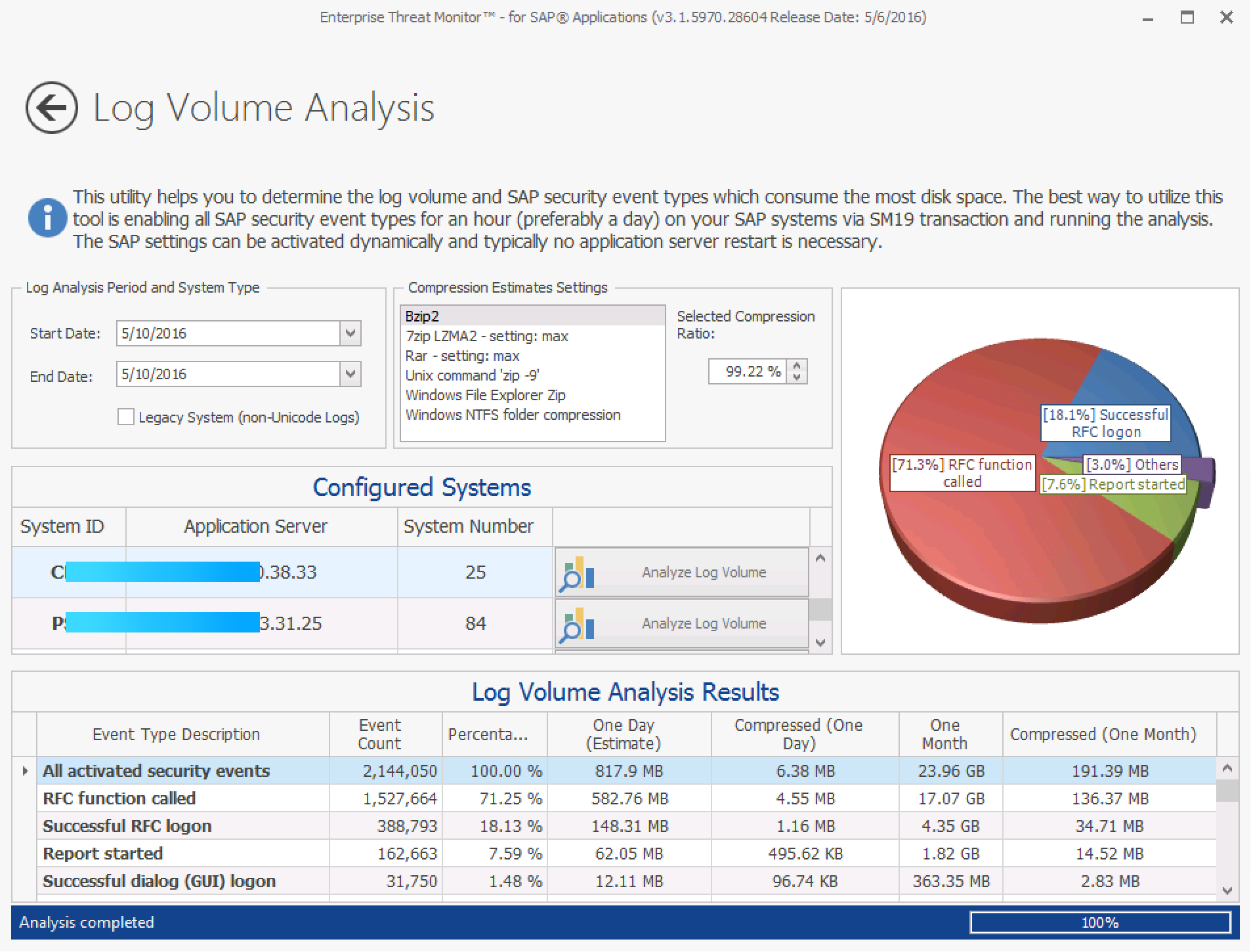
What is SAP Security Audit Log | SAP Security Audit Log analysis | SAP Security Audit Log Sizing and Disk Space | SAP security | Enterprise threat detection for SAP | ETD

SUSE Linux Enterprise Server for SAP Applications 15 GA and SP1 | Operating System Security Hardening Guide for SAP HANA for SUSE Linux Enterprise Server 15 GA and SP1

SUSE Linux Enterprise Server for SAP Applications 12 | Operating System Security Hardening Guide for SAP HANA for SUSE Linux Enterprise Server 12

SUSE Linux Enterprise Server for SAP Applications 12 | Operating System Security Hardening Guide for SAP HANA for SUSE Linux Enterprise Server 12